Running a homelab when you’re interested in a technology field is key to learning new things and keeping skills sharp . I’m also a big fan of free, so you’ll see everything I’ve listed here is free and something you can run yourself (assuming you have the hardware). Here’s my current version, which I’ll break down below.

Overview
I’ve shifted a lot of my lab to the cloud. It helps remove risk from my internal network, helps reduce my required maintenance, and running infrastructure on the cloud helps hone a different set of skills than what’s required for running things on a private network. For the sake of this post, I’ve also excluded network components that aren’t lab related (such as home automation).
| Server/Service | Function |
| Cloudflare (service) | DNS/Proxy/WAF/Tunnel |
| Cribl (service) | Logging |
| SumoLogic (service) | Logging |
| Axiom.co (service) | Logging |
| KASM (VPS) | Virtual Desktop/Apps |
| Splunk (VPS) | Logging |
| OpenCTI (VPS) | Threat Intel |
| TPOT (VPS) | Honeypot |
| Sandfly Security (VPS) | Linux Security |
| Velociraptor (VPS) | Endpoint Forensics |
| badpwd.com (VPS) | Website Project |
| SophosXG (VM on Physical Host) | Primary Firewall |
| PFSense (VM on Physical Host) | Lab Firewall |
| PiHole (VM on Physical Host) | DNS Server |
| Cribl Agent (VM on Physical Host) | Log Shipper |
| AD Lab (VMs on Physical Host) | Isolated Lab Environment |
Logging
A core component of my lab relates to logging. I’m routing all of my logs through Cribl cloud. Internal logs go to the Cribl Agent which then ships to Cribl cloud. Once the logs are in Cribl, I keep a copy in Cribl Cloud and then ship them to Axiom.co as my primary SIEM and a subset of logs are then shipped to SumoLogic where the logging volume is only 500MB.

I have a Splunk server that I self host as the free version isn’t available as a cloud service. I only ship data here as needed due to free license limits. The free version also lacks authentication, so I host it behind my KASM server with access restricted to the KASM IP only, allowing me to have some form of access control. Speaking of access control..
Access
Cloud access control is managed by firewall rules where possible, but in many cases access control is handled by Cloudflare. For example, my badpwd.com webserver needs to be reached by anyone on the internet, so I use a Cloudflare tunnel to pass web traffic to the VPS. Management of the host needs to be limited to just me, so I use a different tunnel to limit SSH access.
KASM is another key component of my lab, and is worthy of it’s own post (highly recommend you check it out!). Access to my KASM is passed through another Cloudflare Tunnel, and access into the KASM instance is managed with user credentials. While KASM provides access to a number of applications like TOR, Terminal, or Maltego, I also have some custom apps that make KASM function like a gateway, like I previously mentioned about Splunk.

App Breakdown
- Cloudflare (free)
- I’m using DNS, WAF, Tunnels and even R2 storage. It’s a flexible service and the free features can’t be beat.
- Cribl (free)
- I’m using Edge for shipping logs, Stream for transporting and transforming those logs, and Lake/Search for storage and search of up to 50Gb/30 days of logs, which is plenty for a lab.
- SumoLogic (free)
- I’m using SumoLogic as a log destination in Cribl and using the 500mb daily log ingest for some endpoint logs and misc log source.
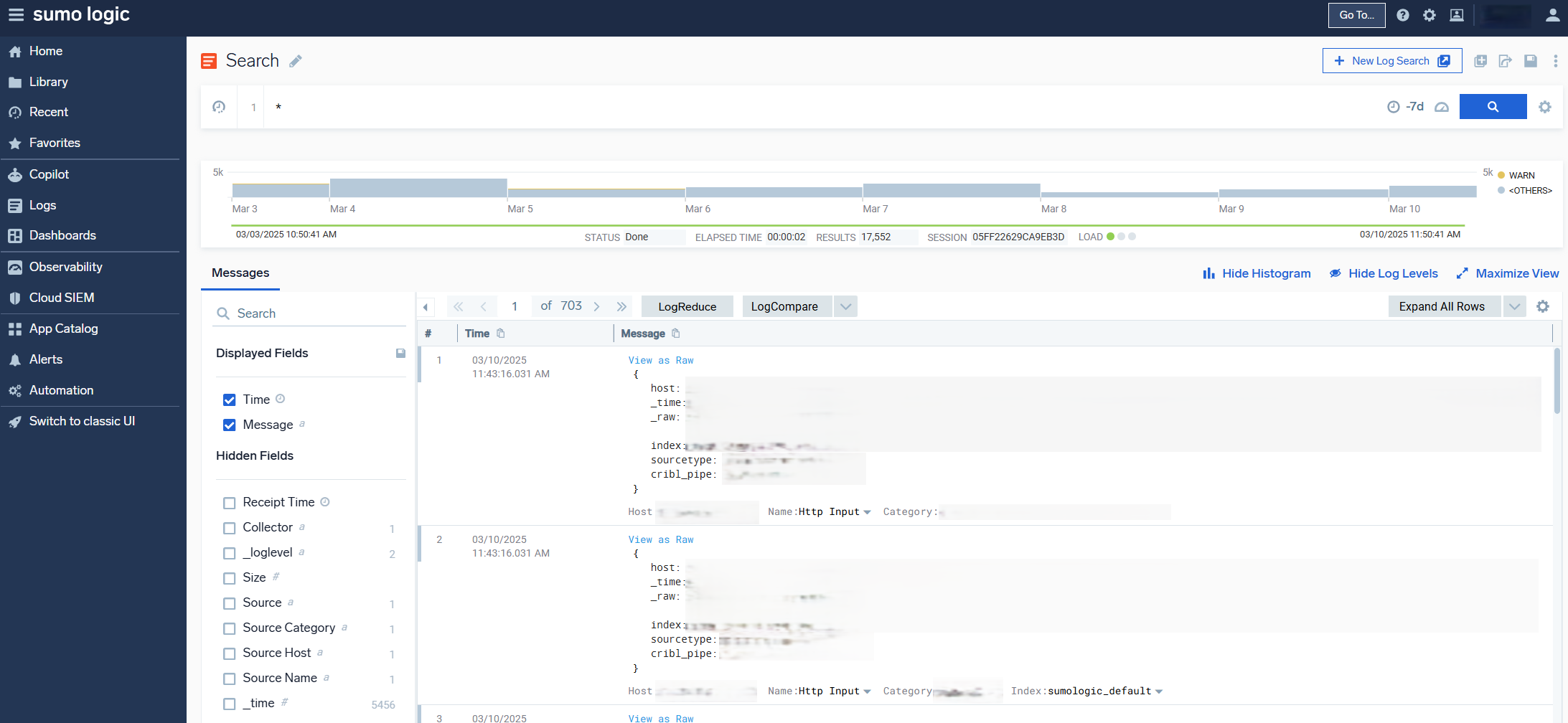
- I’m using SumoLogic as a log destination in Cribl and using the 500mb daily log ingest for some endpoint logs and misc log source.
- Axiom.co (free)
- I’m using Axiom as my primary log destination as the free tier provides up to 500gb of log ingest with a 30 day retention. It’s an up and coming platform and the free tier is very usable.

- I’m using Axiom as my primary log destination as the free tier provides up to 500gb of log ingest with a 30 day retention. It’s an up and coming platform and the free tier is very usable.
- Splunk (free, but I pay for the VPS it runs on)
- I’m using Splunk as my trusty logging tool (I know SPL better than the other logging tools I have), however the 500mb daily log ingest makes the use limited. I primarily use it to review static datasets (like large CSV datasets)
- KASM (free, but I pay for the VPS it runs on)
- I’m using KASM to host a number of containers, though I primarily use it for the web browser, Maltigo, and access to my Splunk server
- OpenCTI (free, but I pay for the VPS it runs on)
- OpenCTI is where all my threat intel lives (look for a future blog post on that soon). I’m working on growing the use of this for proactive blocking and reactive log review of new indicators.

- OpenCTI is where all my threat intel lives (look for a future blog post on that soon). I’m working on growing the use of this for proactive blocking and reactive log review of new indicators.
- TPOT (free, but I pay for the VPS it runs on)
- TPOT is my trusty honeypot and something I’ve run for years as something to play with and gather intel. TPOT is the one service on this list I would NOT feel comfortable running in a lab inside my network.

- TPOT is my trusty honeypot and something I’ve run for years as something to play with and gather intel. TPOT is the one service on this list I would NOT feel comfortable running in a lab inside my network.
- Sandfly Security (free, but I pay for the VPS it runs on)
- Sandfly is a newer addition to my lab, but I appreciate having some security tooling on my Linux hosts.
- Velociraptor (free, but I pay for the VPS it runs on)
- Velociraptor is one of my favorite tools that I’ve used for actual IR cases. I don’t keep hosts connected to it full time, but I do add hosts for testing and for forensic review. (No screenshot, sorry not much to see)
- badpwd.com
- This is a honeypot project I run. It’s been a project to learn python and I enjoy being able to share intel, even if it’s low value.

- This is a honeypot project I run. It’s been a project to learn python and I enjoy being able to share intel, even if it’s low value.
- SophosXG (free but I pay for the hardware the VM runs on)
- I believe that SophosXG is the closest you can get to a free enterprise firewall. It’s full featured and works very well. I run it as a VM but it connects to my ISP modem as my primary firewall. It’s provided years of service from way back when it was only UTM.

- I believe that SophosXG is the closest you can get to a free enterprise firewall. It’s full featured and works very well. I run it as a VM but it connects to my ISP modem as my primary firewall. It’s provided years of service from way back when it was only UTM.
- PFSense (free but I pay for the hardware the VM runs on)
- PFSense is a good solution, but I use it to firewall and route traffic from my Active Directory lab.
- PiHole (free but I pay for the hardware the VM runs on)
- PiHole logs my DNS traffic and helps keep the ad volume down. Great service that I’ve been running for years.
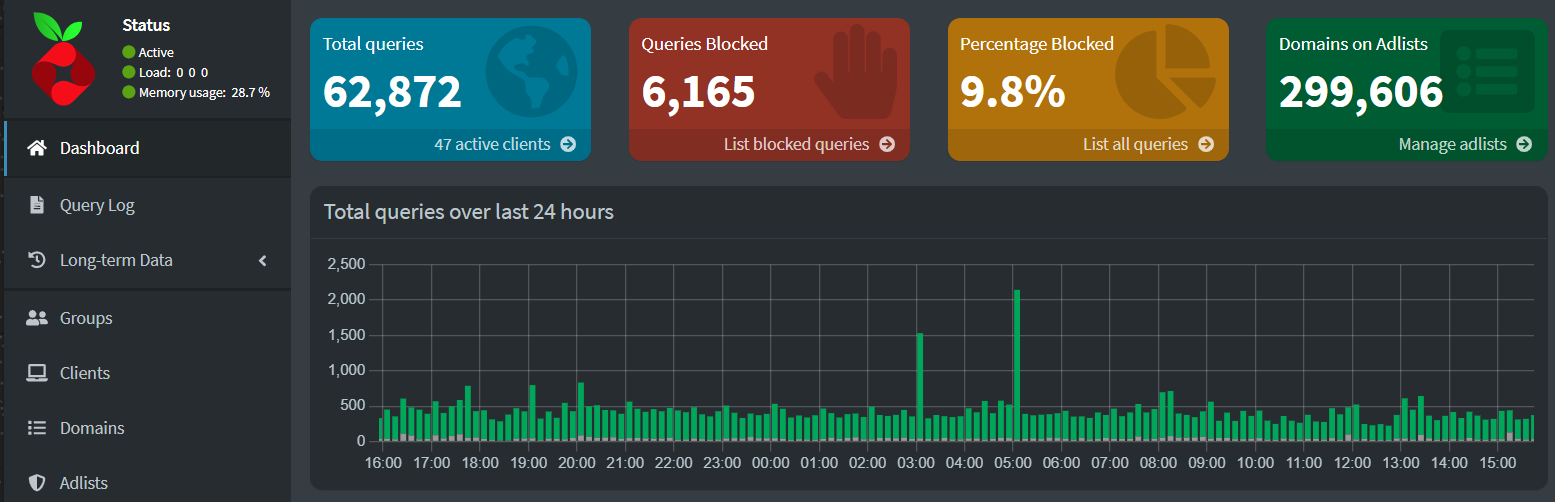
- PiHole logs my DNS traffic and helps keep the ad volume down. Great service that I’ve been running for years.
- Cribl Agent (free but I pay for the hardware the VM runs on)
- I needed a way to ship internal logs like the firewall and DNS logs to Cribl. The Cribl Fleet Agent runs on a Linux VM and accepts logs over syslog to ship to my cloud SIEMs.
- AD Lab (free but I pay for the hardware the VM runs on)
- There’s more than one VM here, but it’s just a standard domain with workstations and a Kali box for offsec testing.
Challenges
Even with moving services to the cloud, I still have challenges keeping things running smoothly. The biggest issue is keeping everything up to date. OpenCTI, Velociraptor, and Splunk don’t have auto update features and it’s difficult to stay on top of updates.
The free logging solutions don’t have a great security stacks built in. No prebuilt security rules mean a lot of manual work to get something going. While Sandfly Security isn’t a logging solution, it does a good job of managing alerts and helps me keep on top of lab security.
I don’t have a good backup solution in place. There’s not much I’d lose sleep over losing, but saving my OpenCTI config would save me some time if I needed to rebuild it again.
