We all know that there are vulnerable things on the internet, but for some reason I’m always left surprised by how many vulnerable or compromised things there are floating around out there. During some Holiday time off in December, I spent some time getting familiar with the LeakIX.net platform which provides a front row seat to browse these vulnerabilities.
What’s LeakIX?
Like Shodan or Censys, LeakIX is another internet search engine that crawls and indexes services, documenting findings with a focus on vulnerabilities. Depending on the finding age or severity, some findings can be accessed by anyone and some require a paid user account with identity verification.
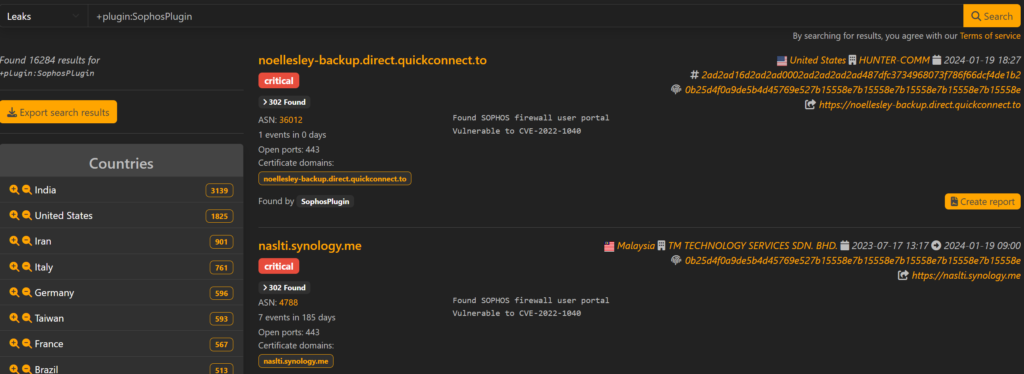
What drew me to LeakIX was the ability to submit an ethical disclosure report to the impacted organization. That report includes LeakIX findings and your own summary. Other LeakIX researchers review your reports, and if approved, they’re sent through the platform and LeakIX acts as the proxy between you and the organization so things don’t get “messy”.
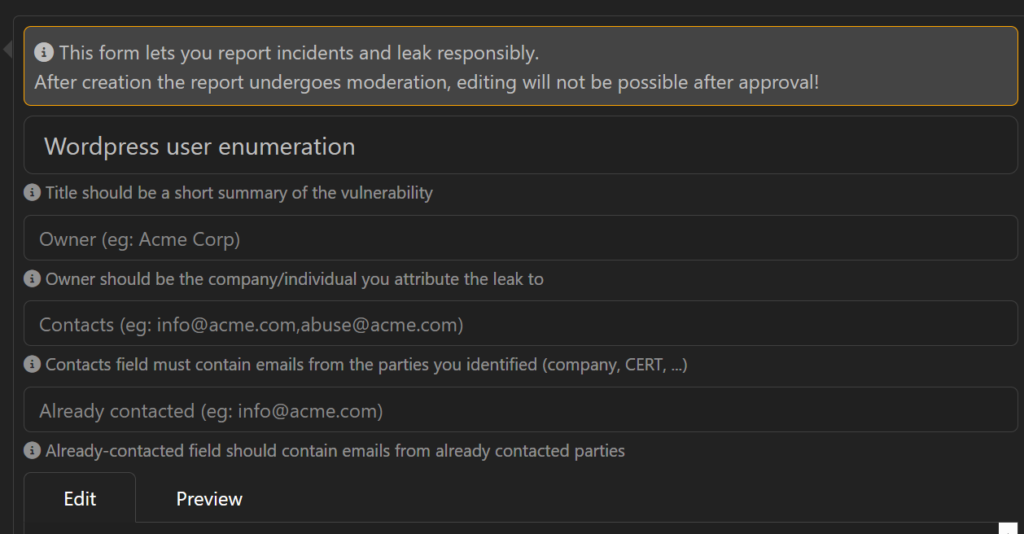
When the Next Vuln Drops
On January 10, 2024, Volexity published a report around exploited Ivanti Connect Secure appliances and on January 15th that they determined the exploitation to be widespread. LeakIX started tracking vulnerable Ivanti Connect Secure instances on January 16th and continues to index new findings. These results are only available to trusted/pro users, so I can’t share them, but I can say there are about 3k IP address findings globally, 900 in the USA alone. These findings also track if the appliance is infected with a webshell, too.
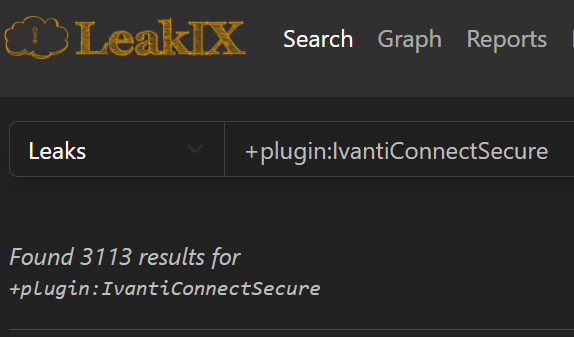
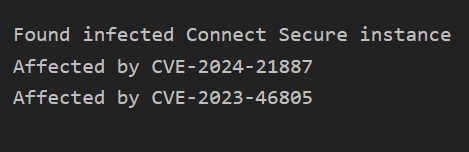
Doing My Part
Do you remember the TV show “Early Edition”? It was about this guy that got a newspaper that showed headline disasters before they happened. The star would go and try and stop these disasters and change the headlines. Seeing all of these vulnerable and compromised systems in LeakIX makes me feel a bit like that.

I’d love to report all of these findings, but one of the biggest challenges is who do you report them to? My typical process works something like this:
- Pick a finding with some information that identifies the vulnerable organization (reverse DNS, certificate domains).
- Spend some time OSINT hunting the appropriate IT contacts for that organization (Google, Linkedin, organization website).
- Send the report and wait for them to fix the vulnerability.
Before the Ivanti vulnerability dropped, I submitted 11 reports through LeakIX for a variety of High and Critical findings I found in December. 2 reports were incorrectly closed by the researcher reviewing the report (another issue for another post), but of the 9 that were submitted and approved, none of my reported findings have been fixed by the impacted organization at the time of this post (about 1 month later). With the new findings related to the Ivanti vulnerabilities unfolding rapidly, I’ve tried a few different methods of contacting impacted organizations. Below are my efforts to alert some organizations impacted by the latest Ivanti vulnerabilities:
- Bug Bounty Report on BugCrowd
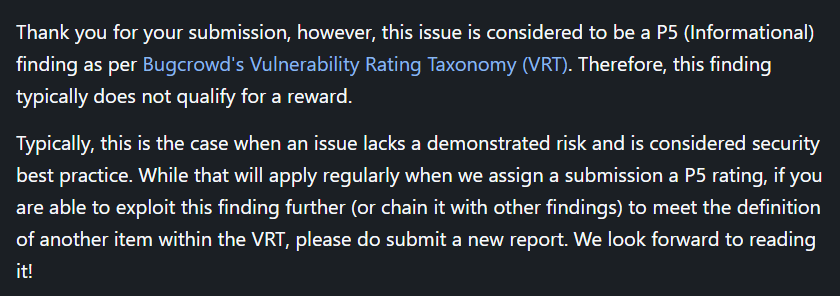
- BugCrowd will let you report a Sev. 1 finding related to an unpatched or out of date system. I submitted my finding to a major manufacturer’s program and received the following email indicating that if I didn’t prove that I could exploit the system, it didn’t count.
- Bug bounty report on HackerOne
- I identified a major airline with a vulnerable Ivanti appliance that uses HackerOne for the vulnerability disclosure program. Unfortunately, HackerOne doesn’t have a category for vulnerable/unpatched systems and I couldn’t submit my finding there.
- Work through a trusted partner
- I identified a major multimedia company with a vulnerable Ivanti appliance and happened to have a contact with a vendor that works with the impacted organization. Working through that contact, they passed along my findings. I never heard back, but as far as I can tell – they’re no longer vulnerable. Maybe my message got through?
- Work through a Senator’s office
- I identified a small state government office with a vulnerable and compromised Ivanti appliance and happened to have a contact with connections to a Senator in that state. While the information was passed along, they’re still vulnerable.
- LeakIX report
- I identified a major electronics manufacturer with a vulnerable and compromised Ivanti appliance and when I didn’t have any other resources to connect with an organization, I submitted a report through LeakIX directly. I’ve not received a response, and their appliance is still vulnerable.
Well Now What?
I have to admit, reporting findings can feel a little hopeless, but even if one is fixed – it will have been worth it. I do enjoy the OSINT hunt to find the appropriate contacts to report to, and I also enjoy monitoring a security situation as it unfolds. It’s only been a few days, so I’ll be tracking these through the attack lifecycle to see if/when they’re fixed, or if some security breach is reported at some point. If anything worth sharing unfolds, I’ll update this post or make another one.
I really like the LeakIX platform and could spend hours crawling through the data they collect. The platform does allow researchers to publish their reports publicly once they’ve been remediated by the impacted organization, and there have been some “happy endings” where findings were fixed. You can also monitor your own organization through the platform, so at the very least you can protect yourself if you can’t protect others!
