I recently built a honeypot with a focus on the capture of passwords that I could use to share results in real-time. I recognize that there are plenty of great honeypots out there (I run an instance of T-POT and am always impressed with how well it was built and all the honeypots it includes), but I wanted something lightweight and something I could build with ChatGPT and badpwd.com was born.

I opted for a SSH honeypot as my foundation to log fraudulent access attempts and capture passwords. I wanted to see what AI was capable of, so I let ChatGPT do some of the work for me.
As recommended by ChatGPT, the honeypot is written in Python using the Paramiko library and writes all attempts to a SQLite database. The production web frontend does not use Flask and I opted for Gunicorn instead. It queries the database to provide near real-time stats (the page refreshes every 5 seconds).
As much as I had hoped ChatGPT would be able to do all of the work, there was a fair amount of debugging I needed to do to get it working. Overall ChatGPT did make things significantly easier, and the project wouldn’t have happened without it.
Architechture
The setup is fairly simple. Against my better judgement, the honeypot and webserver are the same machine which is a tiny VPS I pay about $10 a year for. The honeypot runs on port 22 exposed to the internet and the webserver runs on port 5000 isolated to Cloudflare to prevent the server from leaking the IP and provide CDN and WAF services.
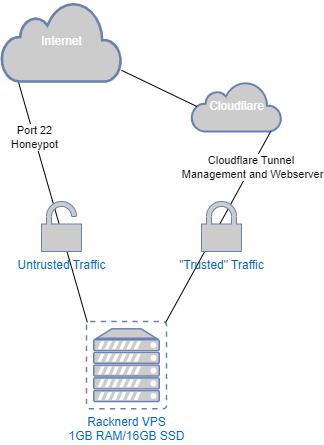
In the future I’d like to move everything but the honeypot to a serverless setup, replacing the database with something like Turso and the webserver with Cloudflare pages. IP and Password lists are already hosted on R2 storage.
Observations
Honeypot daily hits range anywhere from 700 to 15,000 a day. There’s no real pattern to the frequency seen each day.
- The top 5 attacking IPs make up 63% of all attacks to date. The top IP geolocates to India and looks like it may be a compromised Mikrotik device.
- 118.179.155.135 – 29770 attacks
- 218.92.0.100 – 19213 attacks
- 218.92.0.101 – 15810 attacks
- 172.245.206.85 – 13090 attacks
- 188.166.164.250 – 11002 attacks
- The top 5 most commonly attempted passwords are very lame.
- 123456 – attempted 2901 times
- 123 – attempted 1490 times
- 1234 – attempted 907 times
- admin – attempted 720 times
- 12345 – attemted 655 times
- While the attack count continues to grow, the frequency that a new password shows up in the logs has dropped significantly. We’ve been stuck at about 45k unique passwords for a long time. To put that into perspective, the entire RockYou password list contains over 1mill passwords.
If you’re interested in honeypot analysis, there are some great writeups that are worth checking out:
https://isc.sans.edu/diary/What+is+the+origin+of+passwords+submitted+to+honeypots/30182
https://systemoverlord.com/2020/09/04/lessons-learned-from-ssh-credential-honeypots.html
